As technology to fight scam calls continues to evolve, so do the scams themselves. Ten years ago, scammers could phone it in – literally – and cold call thousands of numbers, finding plenty of potential victims. Now, fewer people are willing to answer unwanted calls than ever, so they’re getting a lot more creative in their attempts to money grab.
Last year, we noticed a new trend we called Enterprise Spoofing – scammers using information from massive corporate data breaches to personalize and hyper-target victims. By combining a quality-over-quantity approach to calling with personalized information about the caller, scammers can now appear more legitimate than ever.
This trend isn’t just a theory, though. Last month, we were alerted to a situation on Twitter where this exact thing happened.
Twitter user @anothercohen received an automated robocall saying his “iCloud account was compromised,” so he decided to connect with the live caller to see how they might try and scam him. The man on the other end told him his account had been hacked and proceeded to verify his full name AND Apple ID email.
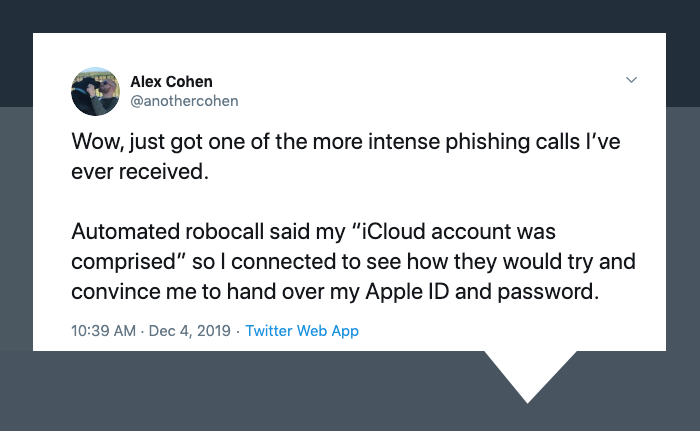
When asked where he got that information, the caller abruptly hung up.
What’s even scarier? The scammer used spoofing technology to mirror Apple’s main number (1-800-MY-APPLE), which is programmed into every single iPhone automatically.
Thankfully, this Twitter user caught on to the scheme before giving up any information, but a less tech-savvy person could easily see a call from Apple and assume it’s legitimate, especially if the caller had their Name and Apple ID on hand.
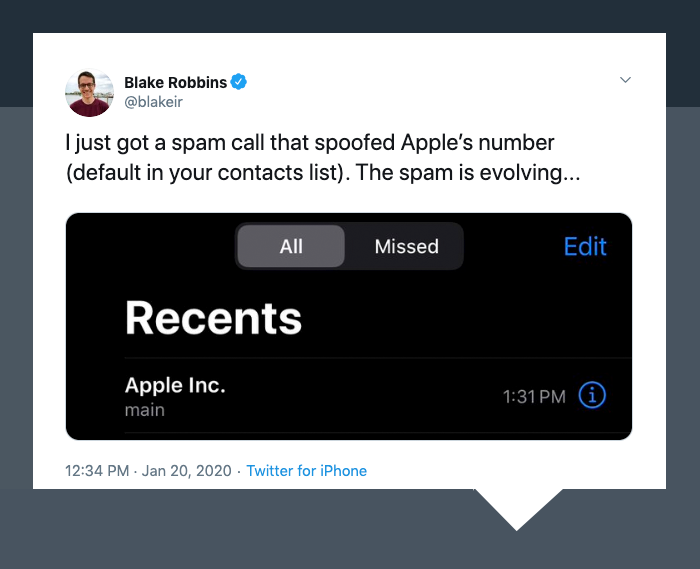
This isn’t an isolated incident, either. Twitter user @blakeir tweeted he too had received a call spoofed from Apple’s number, a default in iPhone user’s contact lists. Without the security of a verified call, Apple’s reputation gets tarnished by these scammers, and legitimate calls from their number could go unanswered.
So what’s the answer to this problem? Obviously, much of the burden lies on the businesses themselves to avoid data breaches in the first place. But a “don’t get got” strategy alone isn’t enough to keep their customers – and their good name – safe. We recommend a more proactive approach: branded, verified calling with our Engage product.
As long as scammers can spoof, a phone number is all they need to start an elaborate scheme. With Engage, we estimate there’s a one in a billion chance that anyone could spoof a verified, branded call, thanks to a pretty sophisticated system of checks and balances we’ve built into our database. Plus, Engage makes it easier for consumers to trust their phones and answer them, because it’s clear who’s calling and why.

Here’s a mockup of what an Engage call from Apple might look like.
If you’re looking to be proactive about protecting your consumers from predatory calls, let’s talk. We can ensure you’re reaching your customers on millions of handsets – and more importantly, that they’re answering when you need them to. Check out the Engage demo and request more information here.



